For Hyper V to replica between 2 different domains, we must enable certificate based authentication, preferable a wild card certificate. Our scenario, Hyper V 2012R2 with 2 nodes cluster on primary site (cluster name MYRSVMH8.primary.local). On the replica site, Hyper V 2012R2 with 2 nodes cluster (cluster name is HVC02.replica.local). This is assumed your cluster is configured and running.
In summary, the steps are
1. Pre-stage replica broker object
2. Create cluster replica broker
3. Generate certificate for authentication
4. Enable replica broker on replica site
5. Host files
6. Configure VM for replication
7. Configure storage location on replica site
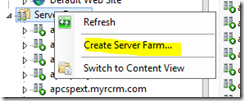
Pre-stage the computer objects
1. Pre-stage a computer object in the Hyper-V OU that is the name of the Replica Broker role you wish to create (e.g. Replica). Once the object is created, you will then need to go to the Security tab, add the cluster computer object; finally, give it full control.
Here you can see the pre-staged computer object I created in my Hyper-V OU:
![clip_image001[4] clip_image001[4]](http://lh4.ggpht.com/-n3cdFRk57MM/VSXDw6mPO5I/AAAAAAAABCU/igYlgfExwHc/clip_image001%25255B4%25255D_thumb.png?imgmax=800)
2. After creating the object, called REPLICA, I right-clicked on it then went to the Security tab. Next, I added the Cluster computer object and gave it full control. (In this screenshot, you’ll notice my cluster is named HV1-HV2-2012CLU.) Click Apply then OK.
![clip_image002[4] clip_image002[4]](http://lh5.ggpht.com/-9WP9G2eJp08/VSXDx8lA5dI/AAAAAAAABCk/BvjF6Lu7Nn4/clip_image002%25255B4%25255D_thumb.png?imgmax=800)
![clip_image003[4] clip_image003[4]](http://lh3.ggpht.com/-8jiGaud5RcA/VSXDzci0_2I/AAAAAAAABC0/9_kd6OBT4ZM/clip_image003%25255B4%25255D_thumb.png?imgmax=800)
3. Repeat steps 1 the same on the replica site AD, change the object named to REPLICABROKER
![clip_image004[4] clip_image004[4]](http://lh6.ggpht.com/-DzyXOF_zjKc/VSXD0YWrCPI/AAAAAAAABDE/HNaZDO7CAtA/clip_image004%25255B4%25255D_thumb.png?imgmax=800)
![clip_image005[4] clip_image005[4]](http://lh3.ggpht.com/-V9eD4fKkmQI/VSXD1Ri8X0I/AAAAAAAABDU/RK4V64PyMYQ/clip_image005%25255B4%25255D_thumb.png?imgmax=800)
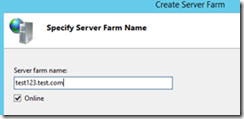
Create cluster replica broker
1. On the primary site cluster node,
2. Open the Failover Cluster
3. Configure Role
4. Select Hyper-V Replica Broker and hit "Next"
5. Add the Name of the replica broker e.g “replica” (Note: this will be translated as an fqdn and also will be add on the domain controller the a record replica.primary.local)
6. Add the IP for the Replica Broker (172.18.70.121), same subnet as management IP
7. Then click "Finish"
![clip_image007[4] clip_image007[4]](http://lh3.ggpht.com/-Tskah30IZjA/VSXD2ubf9QI/AAAAAAAABDg/VcdocvAABhg/clip_image007%25255B4%25255D_thumb.jpg?imgmax=800)
8. Repeat the same on the replica site, change the replica Broker name to “replicabroker”
![clip_image008[4] clip_image008[4]](http://lh3.ggpht.com/-VWA5Cmt1NPg/VSXD3kDbWmI/AAAAAAAABD0/NtEC9smO1D8/clip_image008%25255B4%25255D_thumb.png?imgmax=800)
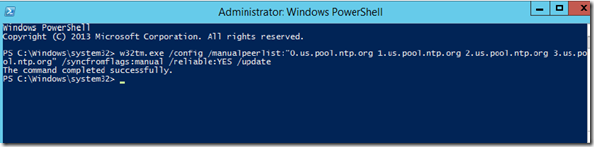
1. Download a tool named makecert.exe on your local machine (window 8, windows 8)
http://www.microsoft.com/en-us/download/confirmation.aspx?id=8279
2. Generate the wildcard certificate for primary and replica site
C:\Windows\system32>cd "C:\Program Files (x86)\Windows Kits\8.0\bin\x64"
# create a root certificate
C:\Program Files (x86)\Windows Kits\8.0\bin\x64>makecert -pe -n "CN=PrimaryRootCA" -ss root -sr LocalMachine -sky signature -r "PrimaryRootCA.cer"
#create primary site certificate, *.primary.local
C:\Program Files (x86)\Windows Kits\8.0\bin\x64>makecert -pe -n "CN=*.primary.local" -ss my -sr LocalMachine -sky exchange -eku 1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2 -in "PrimaryRootCA" -is root -ir LocalMac
# create replica site certificate, *.replica.local
C:\Program Files (x86)\Windows Kits\8.0\bin\x64>makecert -pe -n "CN=*.replica.local" -ss my -sr LocalMachine -sky exchange -eku 1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2 -in "PrimaryRootCA" -is root -ir Loca

3. Export the certificates to all nodes in primary and replicate site
*.primary.local certificate goes to primary site
*.replica.local goes to replica site
4. Open the MMC -> Add/Remove Snap-In -> Add Certificate -> Computer Account -> Next,Next & Finish
5. We go to Personal -> Certificates and with right-click Export the *.primary.local and *.replica.local Certificate. We proceed with Export including the key and the file will be as .pfx also you have to give a password for the certificate.
6. Copy the .pfx file to every Hyper V server,
*.primary.local certificate goes to all nodes in primary site
*.replica.local goes to all nodes in replica site
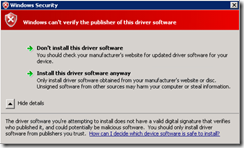
7. Import the certificate on every nodes, to do this,
MMC -> Add/Remove Snap-In -> Add Certificates -> Computer Account -> Next, Next & Finish
then we navigate to Personal -> Certificates -> Right-click and Import -> You must give the password that you have setup on the step 5
8. Copy the primary root certificate to Trusted Root Certificate Authorities
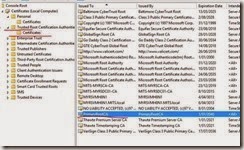
9. Before we proceed with the replica configuration we have to disable the Revocation Check. This we have to do it on every Hyper-V server (primary site (stand alone nodes) and replica site (cluster nodes). To do this we must run this two commands bellow from an elevated command prompt (cmd):
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization\FailoverReplication" /v DisableCertRevocationCheck /d 1 /t REG_DWORD /f
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization\Replication" /v DisableCertRevocationCheck /d 1 /t REG_DWORD /f

Enable replica broker on replicate site
After we have finished with the Import of the CA certificate and the ReplicaSite certificate and also with the disable of the Revocation Check we must select it to the Replica Broker configuration. To do this follow the steps bellow:
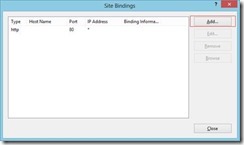
1. Open The Failover Cluster on replica site and Navigate to Roles
2. Right-click on the replica broker and select "Replication Settings"
3. Check the "Enable this Cluster as a Replica Server"
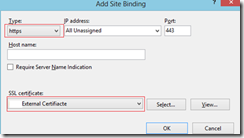
4. Check the "Use certificate-based Authentication (HTTPS)"
5. Specify the port on 443 (leave it as it is)
6. Now you must select the ReplicaSite Certificate that we have created and imported it to the Hyper-V Cluster nodes
7. Specify the Cluster Storage directory
8. And click OK
9. open the Inbound Replica Broker rule on the Advanced Firewall of all Hyper-V nodes (the rule has been automatically created and named as: Hyper-V Replica HTTPS Listener (TCP-In)), for all profiles
Host files
1. Since they are in 2 different domains, they might not use the same DNS server
2. For every nodes on primary site, update the host file to include
172.18.70.120 replicabroker.replica.local
172.18.70.101 HVC02N1.replica.local
172.18.70.102 HVC02N2.replica.local
3. For every nodes on replica site site, update the host file to include
172.18.70.121 replica.primary.local
172.18.70.11 MYRSVMH8N1.primary.local
172.18.70.12 MYRSVMH8N2.primary.local
Configure VM for replication
1. Open The Failover Cluster on primary site
2. Right-Click on the VM you want to replicate and select Enable Replication
3. Just hit "Next" on the first page with the description "Before You Begin"
4. Specify the Replica Server, you must add the FQDN for the replica site (just to mention, all the Hyper-V nodes and the Replica Broker must have access to Internet and have FQDNs in the public dns servers of your Infrastructure so thay can "communicate" also they must have open the port 443 on the local firewall or if you use a dedicated appliance and NAT you must do the Network config there too) for me the FQDN is replicabroker.replica.local and hit "Next"
5. After the Verification of the Replica we must specify the Connection Parameters. The only thing in that page that we must change (of course based on our scenario) is the Certificate, so we must select the Certificate with FQDN that we have been created based on the current server.
6. "Next" on the Replication VHD In the Configure Recovery History you can configure whatever you want on your scenario and "Next"
7. Initial Replication again whatever you want to do on your scenario "Next"
8. "Finish" if all of the above is setup correct you must see the Enable Replication pop-up window and after a second (based on your network) you must see in the Hyper-V Manager on the Status, the percentage of the Replication.
Configure storage location on replica site
1. Locate the VM which you want to replicate to a storage location other than the default you configured in step 1 and right-click the VM, then drag down to Enable Replication.
2. The Enable Replication Wizard starts and takes you through a series of questions to configure replication for this VM. At the Choose Initial Replication Method screen, make sure you schedule the initial replication by selecting "Start replication on" and specify a date. This process will create the initial files and place them in the default location for replicating VM but the files are relatively small in size and can be very easily moved.
3. Now go to Hyper-V Manager, select the VM and choose to move the VM.
4. Select the storage destination you want this VM to replicate to.
5. Return to the primary server where the VM is hosted and where you want to initiate the replication from; to do this, right-click the VM | Replication | Start Initial Replication.
6. Select Start replication immediately. Locate the VM which you want to replicate to a storage location other than the default you configured in step 1 and right-click the VM, then drag down to Enable Replication.
7. The Enable Replication Wizard starts and takes you through a series of questions to configure replication for this VM. At the Choose Initial Replication Method screen, make sure you schedule the initial replication by selecting "Start replication on" and specify a date. This process will create the initial files and place them in the default location for replicating VM but the files are relatively small in size and can be very easily moved.
8. Now go to Hyper-V Manager, select the VM and choose to move the VM.
9. Select the storage destination you want this VM to replicate to.
10. Return to the primary server where the VM is hosted and where you want to initiate the replication from; to do this, right-click the VM | Replication | Start Initial Replication.
11. Select Start replication immediately.























![clip_image001[4] clip_image001[4]](http://lh4.ggpht.com/-n3cdFRk57MM/VSXDw6mPO5I/AAAAAAAABCU/igYlgfExwHc/clip_image001%25255B4%25255D_thumb.png?imgmax=800)
![clip_image002[4] clip_image002[4]](http://lh5.ggpht.com/-9WP9G2eJp08/VSXDx8lA5dI/AAAAAAAABCk/BvjF6Lu7Nn4/clip_image002%25255B4%25255D_thumb.png?imgmax=800)
![clip_image003[4] clip_image003[4]](http://lh3.ggpht.com/-8jiGaud5RcA/VSXDzci0_2I/AAAAAAAABC0/9_kd6OBT4ZM/clip_image003%25255B4%25255D_thumb.png?imgmax=800)
![clip_image004[4] clip_image004[4]](http://lh6.ggpht.com/-DzyXOF_zjKc/VSXD0YWrCPI/AAAAAAAABDE/HNaZDO7CAtA/clip_image004%25255B4%25255D_thumb.png?imgmax=800)
![clip_image005[4] clip_image005[4]](http://lh3.ggpht.com/-V9eD4fKkmQI/VSXD1Ri8X0I/AAAAAAAABDU/RK4V64PyMYQ/clip_image005%25255B4%25255D_thumb.png?imgmax=800)
![clip_image007[4] clip_image007[4]](http://lh3.ggpht.com/-Tskah30IZjA/VSXD2ubf9QI/AAAAAAAABDg/VcdocvAABhg/clip_image007%25255B4%25255D_thumb.jpg?imgmax=800)
![clip_image008[4] clip_image008[4]](http://lh3.ggpht.com/-VWA5Cmt1NPg/VSXD3kDbWmI/AAAAAAAABD0/NtEC9smO1D8/clip_image008%25255B4%25255D_thumb.png?imgmax=800)

